Sensitive data protection
- Published
- 5 min reading

World Wide Warfare
Blocking company operations, intellectual property theft or crucial information leak – these are just some of the examples of the greatest cyber security threats. How can we counter them?
In 2004, a former employee of the web giant AOL decided to take revenge for his dismissal just a few weeks before. What he did was stealing sensitive personal data: logins and emails of more than 92 million AOL users. The stolen sensitive data was then sold to spammers who used it to send 7 billion spam messages within a few days. The incident can be considered the beginning of the history of personal data theft.
One of the biggest hacker attacks of the last 10 years happened at the expense of Yahoo in 2013. Almost all of Yahoo's users were hacked. Stolen were: passwords, confidential information, birth dates and bank codes, emails and answers to security questions of more than 3 billion users – most important sensitive personal data. This is as many as Facebook, Instagram and Twitter users combined. The consequences were grave. The 2013 attack on Yahoo has been described as the most devastating quantitative attack in history.
Sensitive data
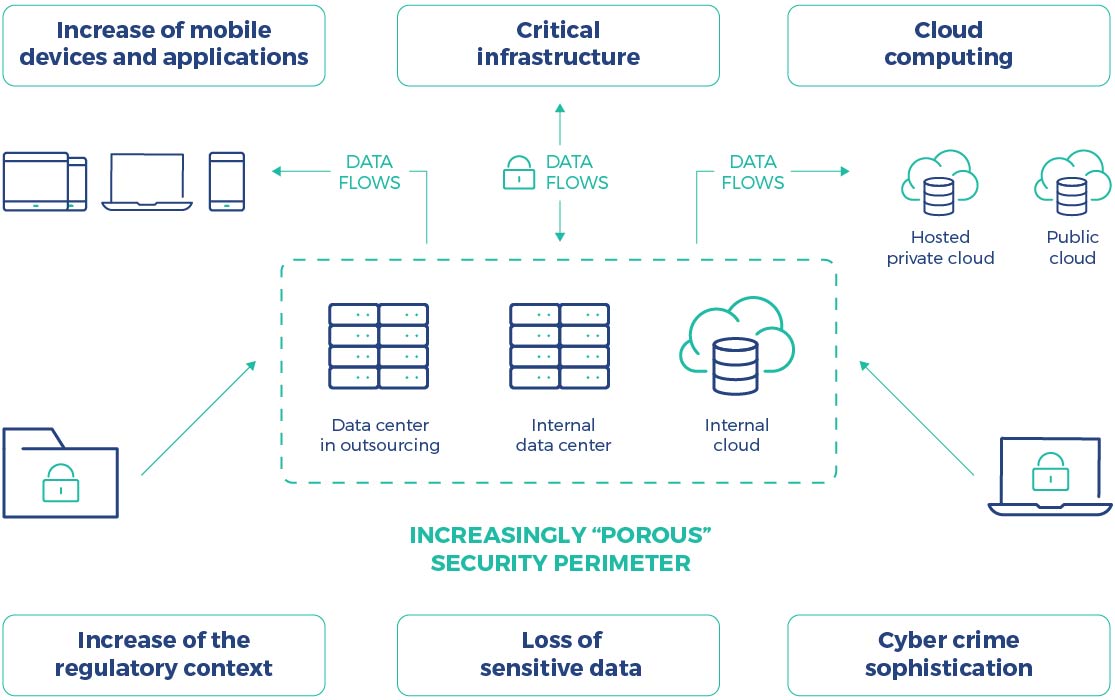
Cyber security becomes indispensable when company information is stored within internal and external data centers, or cloud based systems.
The data centers are the main point of exchange of information flows coming from systems outside the company. Data center security is a fundamental element for all companies that are facing a systematic increase of mobile devices and applications.
Recently, there has been an increasing use of cloud-based applications which, on one hand, are easy to use and guarantee access to documentation from a variety of devices, and on the other, must be subject to strong information security measures.

The development of a cyber security system cannot be separated from the regulatory environment, (e.g. GDPR) and continuous investments are required to guarantee security and protection of critical corporate infrastructure.
Another aspect to take into consideration is the loss of sensitive data that could have reputational, legal and economic impacts. Sensitive information must absolutely be protected regardless of where it is located.
In this context, already complex in itself, it is finally necessary to consider the growing sophistication of cyber-crimes. A system of sensitive data protection must then be constantly monitored and updated in order to guarantee a high level of security.
Know your enemy
Cyberspace is one of the most complex things that man has ever built. Being so incredibly vast, it comes with threats that are many and can lead to a huge damage reputational, financial, legal and operational-wise.
There are three main issues here:
- Modern technologies and, in particular, the IoT, have already increased dramatically and will broaden what experts call the attack surface, i.e. the opportunities to launch malicious attacks. The "always on" lifestyle means, in practice, "more doors and windows" to get in through.
- Our information systems and especially our products, if not properly designed, can be used by attackers as "support bases" and "ports" to launch attacks from.
- The human component is the weak link in the chain and one of the easiest and least expensive “access ports” to be used by an attacker. People who are lured by a phishing campaign, who use the name of their cat or son as a password, or the same smartphone as their kids are the first ones to open the doors to cyber criminals. Sites, networks and databases of their organizations are then at considerable risk.
Confirming humanity
Two key elements of IT security solutions are user authentication and authorization. The first confirms the identity of a user, while the second guarantees the user accesses a specific resource at specific times and for specific reasons.
Cyber security is one of the cornerstones of Comarch's business, and the tPro solutions in token and mobile versions guarantee better user experience in managing electronic identity for financial sectors.
Concerning the management of authorizations or access to sensitive programs and data, Comarch offers the Identity and Access Management (IAM) system, a tool for identifying, authorizing, authenticating and managing user access to applications, VPNs, workstations and sensitive data.
The threats to IT security are becoming more frequent. At Comarch, we optimize and develop our solutions to provide our customers with the most advanced IT systems able to deal with such cases and eliminate risks.
